In today's digital landscape where cybersecurity is paramount, Cloudflare emerges as a powerful shield against malicious bots and cyber attacks. However, what happens when legitimate data access or task automation is required? This detailed guide explores proven techniques and methodologies for navigating Cloudflare's security measures.
Whether you're a data extraction specialist, automation expert, or technology enthusiast, this comprehensive post will help you understand and work effectively with Cloudflare's protective infrastructure.

1. Understanding Cloudflare Bot Protection
Before exploring effective bypass strategies, it's essential to understand what Cloudflare is.
Cloudflare Bot Protection, developed by a leading cybersecurity company, is integrated into Cloudflare's Security Operations Center (SOC)-as-a-Service. This comprehensive solution caters to businesses of all sizes, delivering essential services including security monitoring, incident management, and threat identification.
The Bot Management system is specifically engineered to handle sophisticated bots capable of bypassing traditional CAPTCHA systems and engaging in malicious activities like credential stuffing, credit card fraud, inventory manipulation, DDoS attacks, content spamming, and similar threats. However, the system maintains allowances for legitimate bots including search engine crawlers, AI chatbots, digital assistants, and authorized web scrapers.
For professionals and organizations dependent on large-scale data extraction, the Bot Management system can present significant challenges. Websites protected by Cloudflare actively block automated access attempts. Multiple access attempts typically result in error notifications such as "Error 1012: Access Denied" or "Error 1015: Rate Limit Exceeded."
To address these challenges effectively, understanding proper bot protection mitigation strategies is crucial. This requires a deep understanding of Cloudflare's detection mechanisms, which will ultimately enable more successful navigation of these security measures.
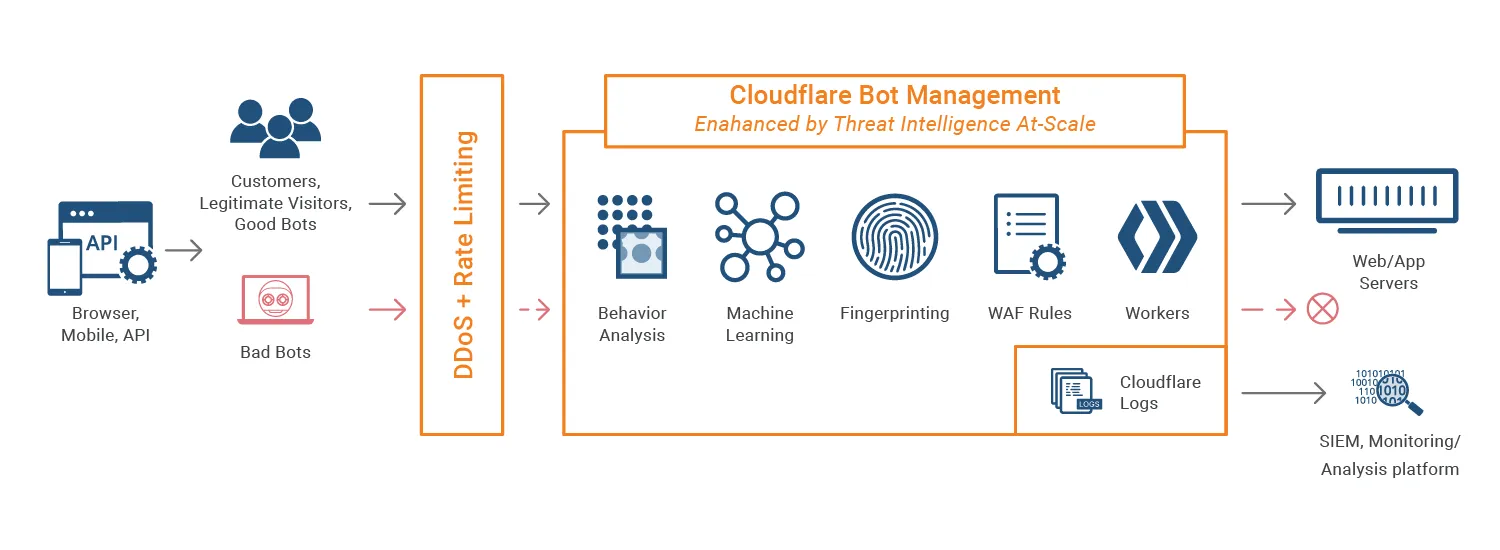
2. Bot Detection with Cloudflare
Digital bots are ubiquitous, and Cloudflare implements sophisticated detection methods. Their approach combines both active and passive detection techniques. Let's examine these methods in detail, complete with practical examples and insights.
2.1 Passive Bot Detection Methodologies
Passive Bot Detection operates like invisible surveillance systems, monitoring automated activities without immediate intervention or blocking.
Botnet detection based on IP address and its fraud score
Simply using any IP address won't guarantee Cloudflare bypass. The platform employs sophisticated behavioral analytics to monitor botnet activities. It tracks patterns of automated behavior and maintains databases of suspicious IP addresses and devices. Requests from these flagged sources face immediate restrictions.
Each IP address carries a risk or fraud score that reflects its reliability. This score considers multiple factors: the reputation of the associated Internet Service Provider (ISP), the IP's geographical location, and its origin source. Cloudflare evaluates these scores carefully, implementing restrictions on bot activities from IPs associated with questionable ISPs, suspicious locations, or dubious sources.
Checking the HTTP request headers
Cloudflare implements detailed analysis of HTTP request headers to differentiate between human users and automated systems. Requests lacking standard browser headers or originating from non-traditional browsers are typically identified as automated and subsequently blocked.Use of TLS fingerprinting
Transport Layer Security (TLS) fingerprinting is a key component of Cloudflare's detection system. Different devices and software create unique fingerprints, and during TLS connections, they transmit "client hello" messages containing encryption specifications. Cloudflare cross-references these messages with user-agent headers, allowing legitimate requests while flagging suspicious ones.HTTP/2 fingerprinting technique
HTTP/2 headers play a crucial role in bot identification. This modern protocol enhances web security while enabling header field compression and multiplexed requests. The binary framing layer creates distinct fingerprints for each request, which Cloudflare validates against its database. Similar to TLS fingerprinting, HTTP/2 fingerprints must match whitelisted patterns for successful request processing.
2.2 Active Bot Protection Methodologies
Active bot detection involves direct verification of visitor authenticity through various challenges and checks. Here are the primary active detection methods employed by Cloudflare.
CAPTCHA usage
CAPTCHAs remain a fundamental bot detection tool, often implemented pre-login to challenge automated systems. These tests leverage human cognitive abilities to interpret specific patterns and images. While Cloudflare utilizes CAPTCHAs, their implementation varies based on factors including website configuration, traffic patterns, and browser characteristics.Event tracking
Human browsing behavior exhibits natural patterns in keyboard and mouse usage. Automated systems typically display mechanical patterns, characterized by rapid requests, minimal keyboard interaction, and limited mouse movement. Cloudflare analyzes these behavioral patterns to distinguish between human and automated traffic.Canvas fingerprinting
This sophisticated technique captures specific browser characteristics including graphics hardware and rendering engines. These elements combine to create unique identifiers that help track users across different websites. Cloudflare leverages canvas fingerprinting to identify and filter automated traffic based on these distinctive patterns.Browser fingerprinting
Browser fingerprinting creates unique device identifiers by analyzing multiple attributes including display specifications, browser type, and installed extensions. Cloudflare employs this technique to track individual devices accessing protected websites. Repeated appearances of identical fingerprints may trigger bot detection algorithms. This method is particularly effective against bots that frequently alter their user-agent strings while maintaining other device characteristics.Environment API querying
API querying collects comprehensive environmental data including operating system details, browser specifications, and display characteristics. Cloudflare utilizes this information to identify automated systems attempting to mask their identity through modified user-agent strings or similar techniques. By analyzing environmental data patterns across multiple requests, Cloudflare can identify suspicious patterns indicative of automated activity, such as identical screen resolutions across multiple requests.
>>> Learn more: Why Blocking Fingerprinting Doesn't Prevent Account Bans
3. How to bypass Cloudflare Effectively?
Cloudflare's bot detection primarily focuses on IP addresses and browser fingerprints. The browser fingerprint encompasses various elements including user-agent data, canvas fingerprint, operating system information, and screen resolution. Successfully navigating Cloudflare's security requires strategic modification of these key parameters. Effective management of your IP address and browser fingerprint significantly improves your chances of successful access.
3.1 Bypass Cloudflare by changing your IP address
High-frequency requests from single IP addresses often trigger security measures. Cloudflare monitors such patterns and implements access restrictions when detected. Regular IP rotation, particularly between scraping sessions, becomes essential. While both VPN and proxy solutions offer IP changing capabilities, residential proxies typically provide optimal results. Unlike datacenter proxies, which may trigger suspicion, residential proxies generally maintain lower detection profiles.
3.2 Change your Browser fingerprint with Antidetect Browser Hidemium to bypass Cloudflare
The Antidetect browser Hidemium enables creation of multiple profiles with distinct browser fingerprints, facilitating effective Cloudflare navigation. For general CAPTCHA handling strategies, refer to our comprehensive guide on bypass captcha. Hidemium supports diverse proxy configurations including HTTP, Socks 4, Socks 5, SSH, Tinsoft, and TM, allowing proxy integration during profile creation.
Hidemium offers advanced browser fingerprint customization capabilities, allowing users to generate randomized profiles with distinct parameters. These include customizable elements such as user-agent strings, operating system identifiers, screen resolution settings, timezone configurations, Canvas masking, WebGL specifications, hardware concurrency settings, and device memory allocations.
Additionally, for users seeking to streamline repetitive tasks such as account warming, seeding, or website navigation without triggering Cloudflare's bot detection mechanisms, Hidemium's Automation feature proves invaluable. This functionality enables the creation of automated script batches that accurately simulate human-like mouse movements and keyboard interactions across multiple Hidemium profiles.
When it comes to efficient multi-account management and effective Cloudflare bypass, Hidemium stands out as the optimal antidetect browser solution. Beyond proxy integration capabilities, it effectively masks your original digital identity, ensuring authentic human-like browsing behavior.
4. Final thoughts
In today's rapidly evolving digital ecosystem, successfully navigating Cloudflare's security checks has become increasingly critical. Mastering Cloudflare bypass techniques is essential, particularly for professionals in revenue-generating sectors.
Hidemium emerges as a robust solution, offering sophisticated browser fingerprint modification capabilities that enable seamless Cloudflare bypass while maintaining authentic human traffic appearances. Stay competitive and maintain unrestricted online operations by implementing these strategic approaches.
Related Blogs
In the digital age, YouTube is not only an entertainment platform but also a fertile ground for building brands, making money and growing businesses. Whether you are an individual content creator or a company promoting products, increasing views for YouTube videos is a prerequisite for success.However, increasing YouTube views in 2025 is no longer as simple as before. Competition is fiercer,[…]
Affiliate Marketing is one of the most effective ways to generate passive income in the digital environment. Among the popular platforms today, Amazon Associates Stands out thanks to its global reputation, diverse products and high conversion rates.If you are looking to join Amazon's affiliate program and want to know how to get the right marketing link, this article will guide you from A to Z.[…]
In the digital age, owning multiple Gmail accounts is not only a personal need but also a vital factor for people MMO (Make Money Online), marketers or YouTubers. However, mass Gmail registration is often subject to Google checkpoints, requires complex verification and is easily locked. So what is the tool that helps you create mass Gmail safely, avoid checkpoints and save time in 2025?In this[…]
Residential proxies enable breathing of browsing software. Residential proxies are more effective at connecting you than data center proxies since they originate from actual devices. Reading this post right now if you’re unsure about the circumstances under which and from whom to get a residential proxy. What is a residential proxy? In what situations do […]
Play games to earn money and withdraw to MoMo is the hottest trend in 2025. This is a trend that helps you both entertain and increase your passive income every day with just your phone. In particular, you do not need to invest or deposit money, just time, skills and a little patience.If you are looking for those reputable game apps, fast withdrawal to MoMo wallet, the article below by Antidetect[…]
Captcha is a popular security tool used on websites to prevent suspicious activities from automated programs (bots). However, Captcha can sometimes be frustrating for users, especially when fast access is needed or when the Captcha becomes overly complex. In this article, we will explore 7 effective ways to bypass Captcha in 2025, allowing you to overcome these barriers legally and safely.1. What[…]






.png)
