In the context of relationships with cyber security threats as cyberattacks continue to increase, protecting small businesses from cyberattacks has become a top priority. 2025 marks a turning point with many advanced technology solutions that help small businesses improve their defenses without spending too much money.
This article Antidetect Browser Hidemium will introduce Top 13 Cyber Security Solutions rated most effective for small businesses, helping you choose the right tool for data protection, maintain reputation and develop sustainably in an increasingly complex digital environment.
1. Why is cybersecurity vital for small businesses?
For small and medium businesses (SMBs), Cyber Security it’s not just a necessity — it’s the foundation for survival and growth. Yet many business owners remain complacent, leaving gaps open for hackers to exploit. Think about it: you wouldn’t leave your store unlocked overnight, so why leave your online assets exposed?
Menny Barzilay – co-founder of Cytactic – commented:
“Many business owners believe that their company is too small to be targeted by hackers or that it does not hold valuable information. This is a serious mistake.”
The actual numbers are alarming: 73% of small businesses have faced a cyberattack or data breach in the past year alone. SMBs have suffered even higher numbers of social engineering attacks 350%compared to large corporations, simply because they are easier to penetrate.
The damage is not small either. Nearly 40% of businesses attacked last year reported losses.smooth250.000 USD. Besides the cost of remediation, the consequences are widespread: stock price drop, credit rating affected, and interest rates increase.
In addition to money, businesses also spend a lot of time restoring systems, causing disruption to operations and weakening business continuity. The most worrying thing is loss of brand reputation — customers will doubt your ability to protect their information, leading to loss of loyal customers and difficulty attracting new ones.
Faced with increasingly sophisticated threats, SMBs need to adopt Multi-layered cybersecurity solutions to protect from every angle. In the next section, we'll explore cutting-edge 2025 tools and strategies that every small business should implement now.

>>> Learn more: What is Port 443? Its Role and Use in Internet Security
2. Top 13 Cyber Security Solutions for Small Businesses
For small and medium business (SMB), the implementation of comprehensive cybersecurity solutions is key to protecting against the myriad of online threats. An effective security system should ensure Multi-layer protection, overall vision and in-depth analysis.
Thanks to that, businesses not only prevent known risks but also prevent undetected potential hazards.
2.1. Anti-detection browser
Forms of cyber attacksUh malwaregoodonline scam usually relies on tracking users' behavior and browsing habits. To avoid being exploited, you need to hide digital traces and protect your online identity.
Tantidetect browser able disguise identity, hide digital fingerprint, making all your online activities untraceable.
If the business needs anonymous web surfing or Manage multiple accounts marketing services, Hidemium is the optimal solution. This tool supports Completely anonymous web browsing, and allows you to operate multiple social media accounts without restriction.
Originally designed for security purposes, antidetect browsers like Hidemium are now trusted by marketers to expand their digital operations.
With a friendly interface, Hidemium is rated asThe easiest to use antidetect browser, helps protect against identity-based cyberattacks and risk of losing account.
2.2. Antivirus software
According to statistics, 41% of SMBs installed antivirus software or anti-malware over the past year as a mainstay of defense.
This is the first line of defense against dangerous threats such as data theft, system access lockout or device sabotage.
Antivirus software works like this janitor, continuously monitoring and detecting signs of malware before it causes harm.
With the right solution, businesses will be fully protected against virus, worm, trojan, spyware, phishing and ransomware.
2.3. Domain Name System (DNS) Protection
DNS protection acts as a “smart filter” for internet connections, helping to prevent employees from accidentally accessing fraudulent or malicious websites. DNS attacks can redirect users to fake websites, exploit system vulnerabilities, or overload servers, thereby stealing data, breaching security, and spreading malware.
Without this layer of protection, hackers can easily exploit loopholes to trick employees into disclosing sensitive information or clicking on dangerous links, directly threatening the security of corporate data.
.webp)
>>> Learn more: What is a DNS Zone? Benefits and how to manage DNS Zone effectively
2.4. Threat Detection
Threat detection and response systems continuously monitor online activity, proactively looking for signs of danger before they cause damage. These tools can detect malware, ransomware, or sophisticated phishing scams early, helping to stop them in time.
Without a mechanism to detect threats, businesses may only realize the risk when the consequences are too severe — data is stolen, files are encrypted, or systems are completely paralyzed. This is like discovering a leak in a boat after the water has already flooded it.
2.5. Intrusion Detection and Prevention (IDS/IPS)
IDS and IPS are a pair of security technologies that help protect networks from unauthorized attacks. IDS acts as a “gatekeeper,” monitoring network traffic for unusual behavior, while IPS is a “bodyguard” that proactively blocks threats as they arise.
Deploying IDS/IPS helps businesses stop hackers before they can break in, steal data or take control of the system. Conversely, without one, the risk of intrusion and loss of important information will increase significantly.
.webp)
2.6. Next Generation Firewall (NGFW)
Next-Generation Firewall (NGFW) is an advanced security solution that allows in-depth analysis of internet traffic entering and leaving the enterprise. Unlike traditional firewalls, NGFW has the ability to detect and prevent complex network attacks at the application layer, helping to protect the system against threats such as advanced malware or sophisticated intrusions.
In a context where cybercriminals are constantly changing their tactics, NGFW acts as a solid “lock”, strengthening defenses and minimizing risks for businesses.
2.7. Cloud-based security
Cloud Security helps protect data and applications stored on remote server systems. In recent years, attacks targeting cloud infrastructure have increased.110%, while the number of cloud environment intrusions also increased.75%. This makes cloud security an indispensable element.
When businesses apply a multi-cloud environment, security management will become more complicated. Solution Cloud Security Posture Management (CSPM) can support continuous monitoring, configuration assessment, and cloud infrastructure hardening, helping to effectively prevent emerging threats.
Without cloud security, all data — from websites, web applications, customer information to intellectual property — becomes vulnerable to hackers.
2.8. Email gateway security
Email Gateway Security is the first line of defense, controlling all emails sent and received within the enterprise. This system helps eliminate spam, phishing emails, and malware before they reach users' mailboxes.
Email is the favorite attack channel for hackers, when 44% of small and medium-sized businesses suffered a cybersecurity breach in the past year from compromised email systems. Without email security solutions, businesses are at risk of having their data stolen, their accounts taken over, or being infected with viruses from sophisticated phishing campaigns.
>>> Learn more: What is a gateway? Learn more about network gateways
2.9. Enterprise Password Management (EPM) and Privileged Access Management (PAM)
Password management is one of the indispensable security solutions for businesses, especially small and medium-sized businesses. Scott Schober – President and CEO of Berkeley Varitronics Systems – once emphasized:
“One of the leading causes of risk in small businesses is users and employees not creating and managing passwords properly.”
Two important tools are EPM (Enterprise Password Management) and PAM (Privileged Access Management) that help businesses control and protect passwords and important access rights. EPM is like a safe to store passwords, while PAM focuses on controlling access to highly privileged accounts.
The lack of these systems can have serious consequences. For example, last year, INDRIK SPIDER compromised credentials stored in Azure Key Vault and SharePoint due to poor password management. In another attack, SCATTERED SPIDER exploited the lack of a PAM system to generate new administrative access keys, thereby illegally expanding privileges.
Recognizing this risk, many small and medium-sized businesses have proactively increased security: 59% have adopted two-factor authentication (2FA), while 37% have implemented access controls.
2.10. Authentication and VPN Services
Authentication services and VPNs both aim to ensure secure network access, whether employees are in the office or working remotely.
A well-managed authentication system not only prevents unauthorized access, but also encrypts data transmitted over the internet, protecting information from being stolen or tracked. VPNs are also powerful tools for protecting business data, but choosing the wrong provider can be risky. Therefore, prioritizing transparent and open-source VPNs will help ensure maximum security.
Without these services, your network becomes vulnerable to attacks. When sensitive information is stolen, bad guys can easily read and use the data. In contrast, with authentication and VPN services, the data is encrypted so that even if it is compromised, hackers cannot understand and exploit it.
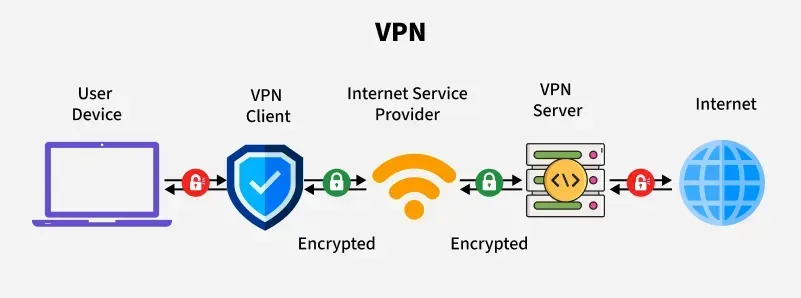
>>> Learn more: Top 10 Best Free VPN Apps
2.11. Endpoint Protection
Endpoint protection is key to securing every network-connected device, from laptops to smartphones. It’s a critical layer of defense that prevents malware and hackers from attacking through the devices employees use to access corporate systems.
For example, when an employee works remotely with an unprotected device, hackers can use it as a gateway to internal systems. Endpoint protection prevents viruses, ransomware, and spyware, keeping the entire corporate network safe.
>>> Learn more: What is the Endpoint? Role and practical application in computer system
2.12. Logging and Monitoring
Logging and monitoring acts as a secure storage for your business, recording every event that occurs on your network. These logs are analyzed to detect anomalies or suspicious activity early, allowing security teams to quickly respond to threats, system failures, or data misuse.
Without monitoring logs, businesses can easily miss warnings of cyber attacks, reducing their ability to prevent them in time and making it difficult to determine the cause when an incident occurs.
2.13. System Recovery
Even with strong security systems, businesses can still become targets for hackers. System recovery is an important backup plan to recover data and get the system back up and running after an incident.
Ensure Recovery Time Objective (RTO) Short response times are key to maintaining business continuity, helping to quickly recover critical systems after an attack. Effective recovery tools minimize downtime, protect productivity and revenue, and are especially important for small businesses.
Lack of planning or ineffective recovery tools can result in lengthy, costly recovery and long-term damage to a business's reputation and profitability.
>>> Learn more: What is a Port? Role and exact classification
3. How to choose the right cybersecurity solution for small and medium businesses
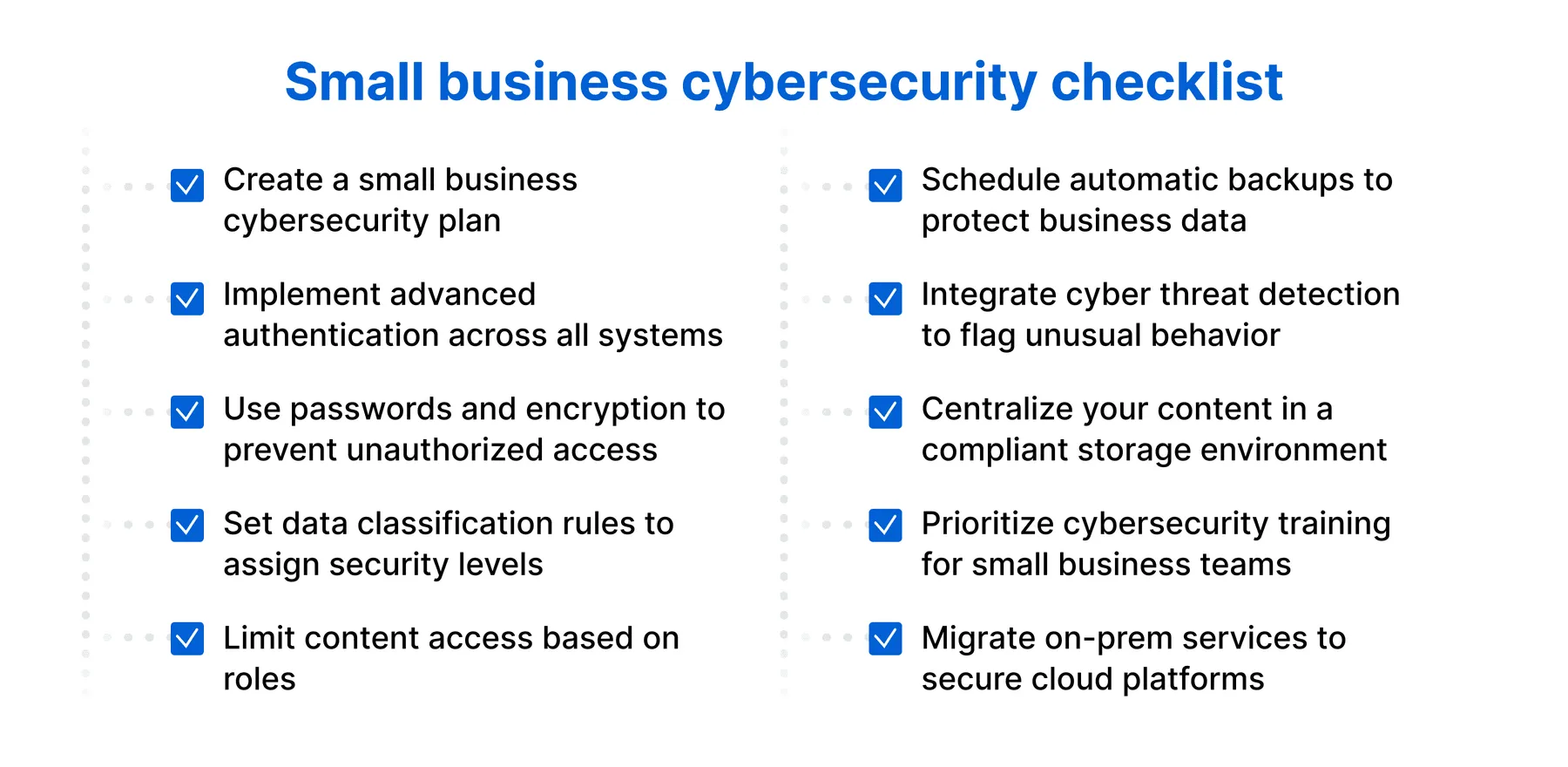
Choosing the right cybersecurity solution for your small and medium-sized business is like choosing quality locks for your doors and windows, providing comprehensive protection against external intrusion risks. Here are the key factors that will help you ensure optimal security for your system:
Multi-layered defense
Prioritize tools that fully integrate functions such as antivirus, anti-malware, email security, advanced threat detection and prevention. Combining these features in a centralized dashboard not only makes it easy to manage but also cost-effective.
Auto update
Security solutions need to support automatic updates so you don't miss out on the latest security patches, just like you regularly change your locks to avoid sophisticated keys that bad guys can use.
Simple, intuitive management
An easy-to-use interface and intuitive analytics tools help your team track and resolve security incidents quickly and accurately.
Automatic data backup and recovery
Continuous data backup capabilities will ensure your digital assets are safely protected, even if the system experiences unexpected failures.
Employee training
Security is not just about technology, it is about people. Good solutions should be accompanied by training programs to raise awareness, help employees recognize and prevent risks such as fraud and network intrusion.
Flexible scalability
Choose a system that can grow with your business, making it easy to scale protection without having to change your entire solution as your business grows.
Multi-device protection range
Make sure your solution can protect every device used in your business, from desktops, laptops to mobile devices, because any device can become a weak point for attackers.
See real customer reviews
Listening to feedback from similar businesses will give you a true sense of the effectiveness and reliability of the solution, helping you choose the right tool for your needs and budget.
4. Conclusion
Cybersecurity today is no longer simply about using regular antivirus software. With the increasing sophistication of cyberattacks, as hackers continue to improve their skills and methods, digital security is more important than ever.
An effective solution is to build a multi-layered security system to promptly detect and handle potential vulnerabilities in the network environment.
Don't let the vastness and complexity of the cybersecurity landscape overwhelm you. Identify the security priorities that are most important to your business and focus on addressing them first.
If you're concerned about identity theft, start by using incognito browsing. This feature hides your digital fingerprint, making it less likely that hackers will track your online activity.
When you're ready to take your security to the next level, try out our anti-detection browser Hidemium With a 3-day free trial and 1000 profiles, you can browse the web more safely and efficiently.
Related Blogs
In the SEO space, many businesses and agencies build blogging strategies from scratch, focusing on optimizing website rankings through quality content. However, a common challenge is Manage multiple Ahrefs accounts for multiple clients or share access that no additional user fees for Ahrefs.Hidemium who share how Share Ahrefs account safely, comply with terms and avoid the risk of being locked[…]
In the context of multi-account management on mobile applications becoming increasingly popular, Geelark Antidetect Browser emerging as a breakthrough solution, specifically designed for diverse needs from affiliate marketing, e-commerce to advertising management. Unlike regular antidetect browsers, Geelark provides an ecosystem cloud phone Unique, realistic Android device simulation, helping[…]
Sẽ không thành vấn đề nếu bạn gọi nó là Twitter hay X, nhưng có một điều chắc chắn là – nếu bạn đã từng cố gắng quản lý nhiều tài khoản Twitter độc lập (“tài khoản X” nghe có vẻ chưa ổn), thì bạn biết đó là một cuộc đấu tranh thực sự để giữ chúng tách biệt và không kết nối với nhau. May mắn thay, đó là vấn đề mà một trình duyệt chống phát hiện như Hidemium giải quyết khá tốt. Nhưng làm thế[…]
What is VPN Proxy Masterand and what makes it the top choice for many users today? It is a tool that supports secure internet access, allows overcoming geographical barriers and protects personal data from cyber threats. In this article, Antidetect Browser Hidemium will provide detailed information about VPN Proxy Master, including the Main features, benefit, as well as How to install and use[…]
Scaling Multi-Accounting: How Proxies Complement Anti-Detect BrowsersIf you have ever done multi-accounting, you know that this activity can lead to a ban. Websites and social networks prohibit managing several accounts at the same time and block violators.However, strict bans do not stop everyone. Many users who work on the Internet successfully bypass them and manage accounts without any[…]


.png)



