In the digital era, Botnet is one of the biggest threats to network security. So exactly What is a botnet?? How to recognize and Prevent DDoS attacks from Botnet effectively? Let's go together Hidemium Find out details in the article below.
1. What is a botnet? Popular attack targets
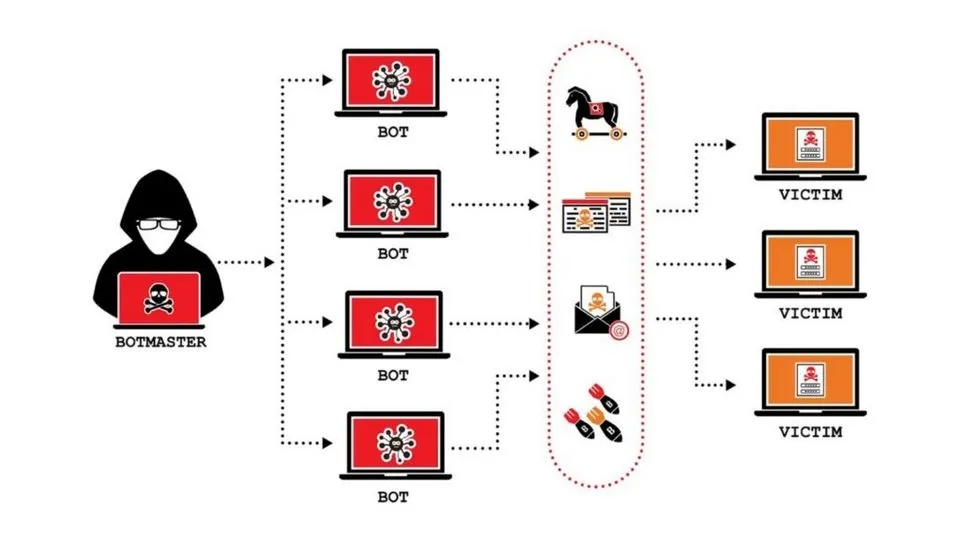
Botnet (short for “robot network”) is a network of infected computers, phones, or IoT devices. malicious code and controlled remotely by hackers. These devices, called "bots", can be used to:
Spreading viruses and malicious code
Distributed Denial of Service (DDoS) Attack
Stealing user data
Disrupting or destroying the server system
These events DDoS Botnet attack It is often large-scale and occurs continuously, causing disruption to websites, banking applications, and online services. The consequences are users cannot access, simultaneously Businesses lose reputation and revenue.
2. Top 7 most popular forms of Botnet attacks today
After understanding clearly What is a botnet?, you need to know more common attack type to take appropriate preventive measures. Here it is 7 forms of Botnet attacks Most popular today:
2.1. Attack DDoS (Distributed Denial of Service)
Hackers use a large network of bots to massively send access requests to the server, causing the system to be overloaded and unable to process. DDoS Botnet Attack causing bandwidth to be exhausted, leading to service interruptions and loss of connection to users.
2.2. Spreading junk mail (Spam)
Unlockable botnets proxy SOCKS v4/v5, then use these proxies to send spam emails to a wide range of users. Additionally, through tools such as packet sniffer, hackers are still possible track and steal sensitive data from the user device.
2.3 Recording keystrokes (Keylogging)
Botmasters can combine with Keylogging techniques to infiltrate the server system, thereby recording the user's keystrokes and stealing sensitive information. Collected data can include Paypal, Facebook accounts and other personal platforms, making it easy for hackers to access information accurately and secretly.
2.4 Stealing user identities
One of the common forms of botnet attack is identity theft through the distribution of junk email (spam). Hackers use fake emails to lure users to fraudulent websites. There, they will collect personal information such as citizen identification numbers, bank accounts, credit cards or tax codes. More seriously, many Botnets also pretend to be state agencies to create trust and force users to provide information.

2.5 Taking advantage of the PPC advertising system
In the process of learning "What is a Botnet" and common forms of attack, users need to be especially wary of advertisements when accessing the Internet. Some Botnets take advantage of Google's PPC (pay-per-click) advertising mechanism — where website owners get paid every time someone clicks. Botnet-infected computers will automatically access and click on ads, creating fake traffic, misleading the system, and affecting the reputation of advertising businesses.
2.6 Botnet distribution
Botnets can also spread through infected software, applications or programs that users accidentally download. These files are often shared via email, HTTP websites or FTP protocols, increasing the risk of infection if users are not vigilant.
2.7 Malicious advertising software (Adware)
Many computers regularly display ads, but not all ads are safe. Some fake adware is designed to deceive users, contains malicious code and is capable of entering the system when the user clicks on it. These software are not only annoying but also pose a serious threat to personal computer security.
3. Harmful effects of DDoS Botnet on businesses
DDoS Botnet is a serious threat to businesses, causing many serious consequences that affect the organization's operations and reputation. Below are typical harms that businesses may encounter when attacked:
Service interruption: DDoS attacks cause server systems to overload, leading to slow or downtime of websites and online services. Users cannot access the system, greatly affecting customer experience and brand reputation.
Loss of control of the system: When a Botnet invades, hackers can take control of devices on the network, perform actions such as sending spam, spreading malicious code, organizing DDoS attacks or stealing data. This causes businesses to lose complete control over their IT infrastructure.
Huge financial loss: Businesses have to spend a lot of money to respond, handle and restore the system after a Botnet attack. In addition, downtime can cause revenue to decline and affect the performance of the entire organization.
Risk of sensitive data leak: Botnets have the ability to exploit security holes in the system to steal important information such as customer data, financial records or business strategies. These risks not only cause losses to businesses but also lose customer trust.
4. How to effectively prevent DDoS Botnet attacks
Understand the concept clearly What is a botnet? will help you realize how dangerous the attacks are DDoS Botnet – serious threat to enterprise systems and data. Below are those solutions Hidemium Recommendations to effectively protect the system:
4.1. Use firewalls and intrusion detection/defense systems (IDS/IPS)
Firewalls are the first layer of defense that help control traffic between the internal network and the Internet, blocking suspicious data packets. Meanwhile, IDS (Intrusion detection system) monitors network traffic and alerts if unusual behavior is detected. IPS (Intrusion Defense System) even proactively reacts by automatically blocking or throttling traffic. When combining firewalls, IDS and IPS, your system will have a solid shield against attacks from Botnet.
4.2. Enhance web application and API protection with WAAP
WAAP (Web Application and API Protection) is a modern technology that helps protect web applications and APIs against forms of attacks such as SQL Injection, XSS and DDoS from Botnets. WAAP monitors access behavior, filters malicious traffic, and detects and neutralizes new threats from Botnets, ensuring system stability and availability.
4.3. Leverage the power of CDN servers
CDN (Content Delivery Network) helps distribute content across multiple servers globally, reducing the load on the origin server and dispersing traffic. This weakens the Botnet's attack effectiveness by routing anomalous traffic to high-capacity POPs. In addition, CDN also supports real-time traffic monitoring and alerts when suspicious behavior is detected.
4.4. Monitor network traffic continuously
Monitoring network traffic is an important step in detecting early signs of a DDoS attack. Dedicated monitoring tools will help you identify spikes or suspicious activity from a specific IP. Thanks to that, you can promptly deploy countermeasures before the Botnet causes serious damage.
In addition, in addition to system-level security measures, you should also pay attention to personal account security and Manage multiple online accounts A safe way to avoid becoming a target for hackers.
>>>Learn more:
How to fix "Network Blocking Encrypted DNS" error on iOS
Latest Viettel DNS & How to Change DNS to Increase Internet Access Speed
Related Blogs
In the context of multi-account management on mobile applications becoming increasingly popular, Geelark Antidetect Browser emerging as a breakthrough solution, specifically designed for diverse needs from affiliate marketing, e-commerce to advertising management. Unlike regular antidetect browsers, Geelark provides an ecosystem cloud phone Unique, realistic Android device simulation, helping[…]
In the context of the increasingly expanding Internet, IP addresses are the core element for connecting and identifying devices. However, many proxy users still encounter limitations when using IPv6 proxies, especially on major platforms such as Google, Facebook, Amazon, eBay, TikTok and many other popular services. So why is IPv6 proxy access limited? Why are mainstream platforms still not[…]
How to Integrate PiaProxy with Hidemium — Complete Privacy at Your Fingertips In today’s digital world, privacy, stability, and efficiency are essential — especially for marketers, developers, and eCommerce professionals managing multiple accounts and geo-targeted operations. Combining Hidemium with PiaProxy brings a powerful synergy — one that enhances anonymity, bypasses restrictions, and[…]
MetaMask is one of the most popular non-custodial cryptocurrency wallets today, supporting the storage of Ethereum-based digital assets and interaction with decentralized applications (dApps). However, because it does not support direct fiat withdrawals, users need to take many intermediate steps to transfer assets to traditional bank accounts.In this article, Hidemium will guide you through the[…]
The choice AweSun – secure remote access software plays a vital role in helping large businesses, freelancers, and remote workers overcome the barriers of connecting and controlling computers in different locations. The right tools will give you the ability to seamless collaboration, session access and remote file transfer fast, efficient troubleshooting support anywhere in the world.To help you[…]
In the digital marketing era, Search Engine Optimization (SEO) is a key factor in helping websites improve their rankings on Google, Bing and other search engines. Well-optimized content will increase the likelihood of appearing in high positions and attracting quality traffic, and make it easy for potential customers to access your product or service. An effective SEO strategy not only drives[…]

.png)





