Digital Footprint, also known as digital footprint, is the sum of all the data you leave behind as you move around the Internet. Every click, post, share, or even search contributes to your online presence.
So why does your digital footprint matter? Because it reflects your entire digital behavior – from what you disclose to hidden data like metadata attached to photos or browser information. This data not only shapes how platforms judge you, but also affects your privacy, security, and sometimes your online reputation.
In an age where technology has become an integral part of everyday life, it is important to understand the scope and impact of Digital Footprint is essential. It helps you be aware of what you're leaving behind online, allowing you to take control of your personal information in a smarter and safer way.
Together with Hidemium, explore your digital footprint further and learn how to manage your online presence effectively – because your personal privacy and security are something you deserve to protect.
1. What is a digital footprint?
Every time you use the Internet, you leave behind a digital footprint – data that records your every action and interaction online. This data is collected through your daily digital activities and is generally divided into two main categories passive digital footprint and proactive digital footprint.
We'll take a deeper look at each type of digital footprint and provide helpful guidance to help you identify, control, and protect your personal information effectively when participating in the online space.

>>> Learn more: What is Canvas Fingerprinting? - The Latest Online Tracking Technology
2. Types of digital footprints and their impact on privacy
A digital footprint is a collection of information that users leave behind intentionally or unintentionally while accessing the Internet. Being aware of these types of footprints helps you be more proactive in controlling your personal data, thereby protecting your privacy when operating online. There are two common types of digital footprints:
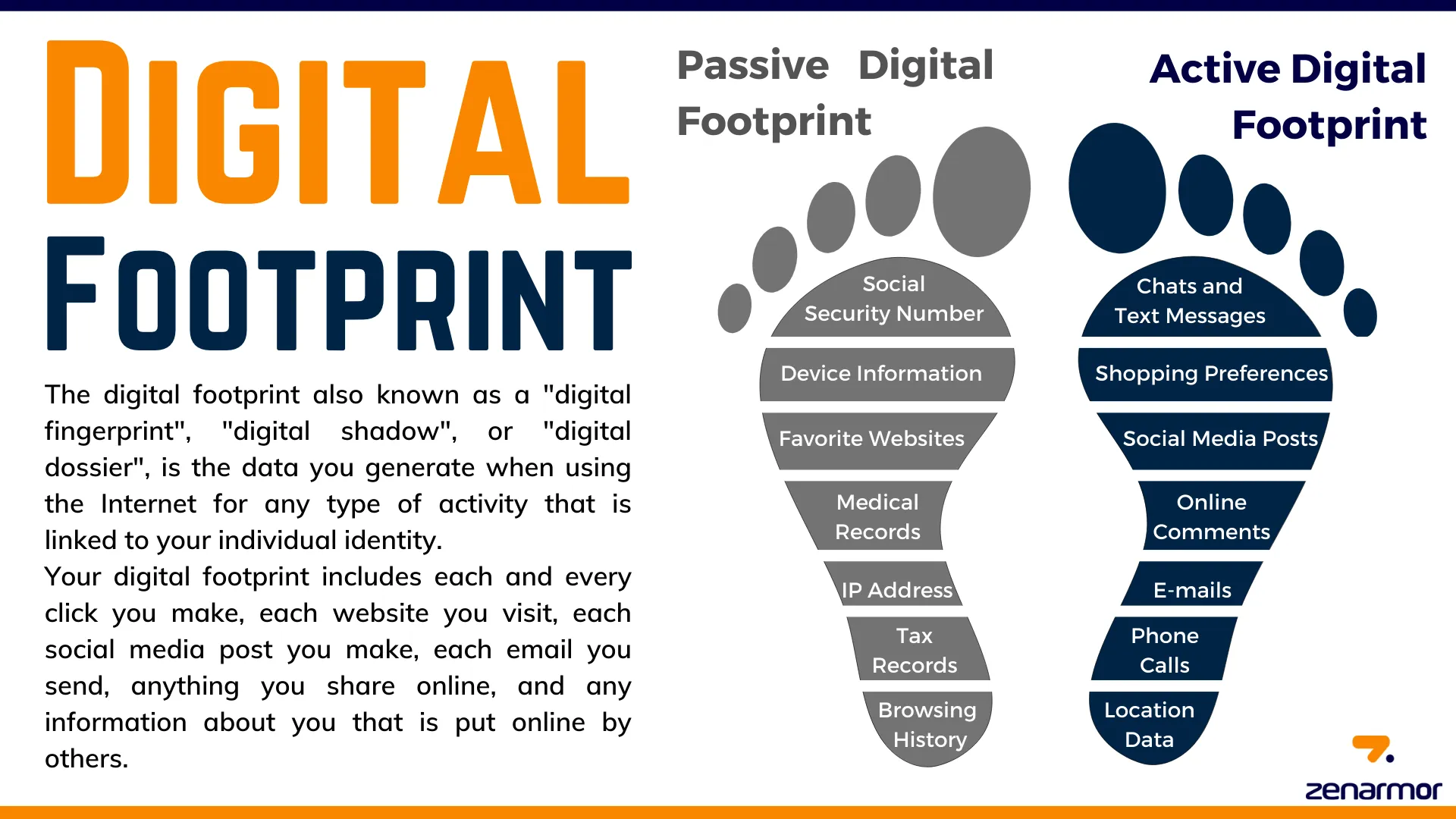
2.1. Passive digital footprint
Passive digital footprints are information collected without direct user interaction – often behind the scenes. Some typical examples include:
Track website activity: Most websites today use cookies and pixels to collect user data, such as IP address, visited pages, time spent on each page...
Data from search engines: The keywords you type and the links you click are recorded by search engines, helping them map out your habits and interests.
Metadata from file: Digital files like photos or documents often contain hidden information (metadata) – such as when they were created, where they were located, or what device they were used on. Even if you don’t share them directly, this data can reveal your behavior or location.
2.2. Proactive digital footprint
In contrast to passive footprints, proactive digital footprints when users intentionally post or share personal information online. Common activities include:
Send emails and messages: Every time you send an email, text message, or participate in a forum, you're creating a data trail related to your identity, the content of your conversation, and the platform you use.
Online Transaction: Every purchase, payment, or online banking activity generates data that can reflect your spending habits and financial behavior.
Social media posts: Photos, statuses, and comments on platforms like Facebook, TikTok, and Instagram all contribute to building your digital profile – expressing your personality, opinions, and interests.
To effectively understand and control your digital footprint, you need to be aware of both types of footprints –passive and active. Managing the information you unintentionally leave behind and what you actively share will help you maintain your privacy and ensure anonymity and build a positive personal image in the digital world.
>>> Learn more: Why blocking fingerprints doesn't prevent account bans
3. What is a digital footprint and how is it created?
In the digital age, nearly every action you take on the internet — from visiting a website, sharing an article on social media, to using apps — creates a digital footprint. These traces are often silent and difficult to detect, but are of great value, because they can be collected, analyzed and exploited for many different purposes such as advertising, personalizing experiences, or even tracking user behavior.
To take better control of your digital identity, you need to understand how these footprints are formed as well as the activities that are silently recording your personal data every day.
Even if you are not proactive, Every interaction with digital technology leaves behind data., and here are the most common ways digital footprints are created:
Web browsing:
Every time you visit a website, browsers and servers can record information such as: pages you viewed, links clicked, how long you stayed on each page, etc. This data not only helps improve the user experience but also contributes to building your digital profile.
Social Media Interaction:
When you post, share photos, videos, or interact with others (like, comment, share), you are creating a stream of data reflecting your interests, habits, and social relationships. This information contributes to the expansion and clarification of your personal digital footprint.
Online shopping:
Every online transaction requires providing information such as full name, address, payment method, etc. In addition, e-commerce platforms also remember your shopping history and consumer behavior to make appropriate product recommendations and marketing campaigns.
Using digital applications and services:
From health tracking apps, movie watching apps, book reading apps to learning platforms, all record data based on your usage behavior. For example, when you exercise, your smart device records your body parameters; when you read documents or watch content, this information is also saved to your digital profile.
4. The role of data collection in shaping digital footprints
Your digital footprint – a digital footprint – doesn’t just happen, it’s created through data collection every time you visit the internet. Here are some common ways your personal data is being collected and why it matters:
4.1. Cookies and behavioral tracking technologies
To personalize the user experience, websites often use cookie and many other tracking technologies. These small files are stored on your device and help remember information such as personal settings, login information, and browsing history. While convenient, they also allow websites to track your entire online activity, contributing to a more detailed digital footprint.
4.2. Behavior analysis and user interaction tracking
Many websites and apps use analytics to better understand user behavior – from how you navigate, to how long you spend on each page, to how you interact with content. The data collected helps businesses improve their products and services. But this information also helps file number personal information without you even knowing it.
4.3. Data from third parties and data brokers
The data broker specializes in collecting and synthesizing information from many sources such as public profiles, social networks, online shopping history... This data is then analyzed to create detailed user profiles and can be sold to third parties or used to serve targeted advertising. This is one of the reasons why users' privacy is increasingly threatened.
4.4. Server logs and metadata
When you access online services, the system will automatically record server logs, including IP address, type of device used, access time and operations performed. Additionally, metadata Emails, files, or messages also reveal information related to your location, time, and internet usage behavior, contributing to an expanded digital footprint that you may not realize.
5. Real-life examples of digital footprints in everyday life
Every internet user leaves behind a “digital footprint” – a collection of data generated from every online behavior and interaction. This footprint not only reflects your personal habits but also contributes to building your digital identity in cyberspace. Here are some real-life examples to help you visualize how your digital footprint is created and grows every day:
5.1. Online shopping
Purchase transaction
When you shop on e-commerce platforms like Amazon, Shopee or eBay, information about the selected product, payment method, shipping address, etc. is recorded. This is the data that contributes to creating a digital footprint - both supporting personalization of product recommendations and reflecting your consumer behavior.
Register an account and receive promotions
Creating an account or signing up for coupons on shopping sites also expands your digital footprint. These sites track your interests and purchasing behavior to provide personalized ads and offers—making your shopping experience more relevant, but also deepening your “digital portrait.”
Use shopping apps
Downloading and using shopping apps (like fashion, grocery, etc.) means you allow these platforms to record your purchase history and spending preferences. This data is used to analyze user behavior and improve marketing strategies.
Sign up for brand newsletter
When you leave your email to receive newsletters from your favorite brands, you are also creating a digital footprint. Personal information can be used to send promotional notifications, introduce new products – serving targeted marketing activities.
5.2. Online banking and financial transactions
Use banking apps
Every time you log into your banking app to check your balance, transfer money, or make a transaction, the system stores this information. This data forms a chain of financial behaviors – an important part of your digital profile.
Online financial investment
When you trade stocks or invest online, your personal information and transaction history are stored by financial platforms. This helps expand your digital footprint in the investment space.
Track financial content
Signing up for a newsletter, reading a blog, or participating in a financial forum clearly demonstrates your interest in the field. Information about the topics you read about is also used by platforms to build a behavioral profile of your users.
Using credit cards online
Credit card transactions – whether purchases or payments for services – are recorded. Credit card data reflects your spending habits and credit history, becoming an integral part of your digital identity.
5.3. Social networks – The place where the most personal information is revealed
Using social media platforms like TikTok, Instagram good Twitter, It's not just about having fun or connecting with friends. Every action you take – from posting, liking, sharing, to interacting with others – contributes to building a digital footprint, helping to shape your identity and social relationships in cyberspace.
Single Sign-On Using your Google or Facebook account when accessing other websites also helps link your personal profile with multiple services, creating a continuous data flow between platforms.
In addition, sharing personal information like photos, locations, life events or political views on social networks will make your digital profile more detailed and clear.
Even when using dating apps like Tinder or Match, the system still records your behavior, interests, and interactions, thereby expanding your digital footprint in the online environment.
5.4. Reading the news – A habit that also creates data
Online news reading habits are also a significant source of digital footprint. When you register an account on online newspapers or magazines, the system will track your reading habits and the content you are interested in.
Through news reading apps, every view, like or interaction behavior is recorded, helping platforms better understand your information consumption behavior.
Job Sign up for newsletter from media organizations or bloggers also contribute to your digital footprint, as you provide your email and show interest in specific topics.
In addition, action Share this post being on social media also indirectly shows that you are following and interested in current social, political or cultural issues.
5.5. Health and Fitness – Private Data Vulnerable to Recording
Today's healthcare devices and apps all contribute to enriching your digital footprint Smart wearable devices like a fitness tracker, it will record data about movement, heart rate, sleep, training goals... and send it to the storage platform.
When you use medical applications to receive advice, make an appointment or save medical information, the system will remember and link this data to the user profile.
Even the gym membership sign up your email address also reflects your interests and exercise habits, becoming part of your digital footprint.
Additionally, if you frequently visit, subscribe to or comment on the health blog, which also helps reveal your personal interests and priorities in this area.
👉 All of these seemingly harmless activities contribute to the formation of digital footprint– your online records accurately reflect your behavior, interests, and identity. Therefore, understanding and controlling how data is collected is essential to protecting personal privacy in the digital age.

>>> Learn more: 7 Free Online IP Fingerprint Checker Tools
6. Managing and Reducing Your Digital Footprint: Protecting Privacy in the Digital Age
In the digital age, every online action – from searching, shopping to social media interactions – leaves a mark digital footprint. These traces can be collected, analyzed and used to track user behavior, even for surveillance purposes.
While data collection provides a more personalized experience, it also poses many risks privacy and personal safety. Data like social media posts, purchase history, geolocation, or information hidden in digital files can all be exploited if you don't have proper protection.
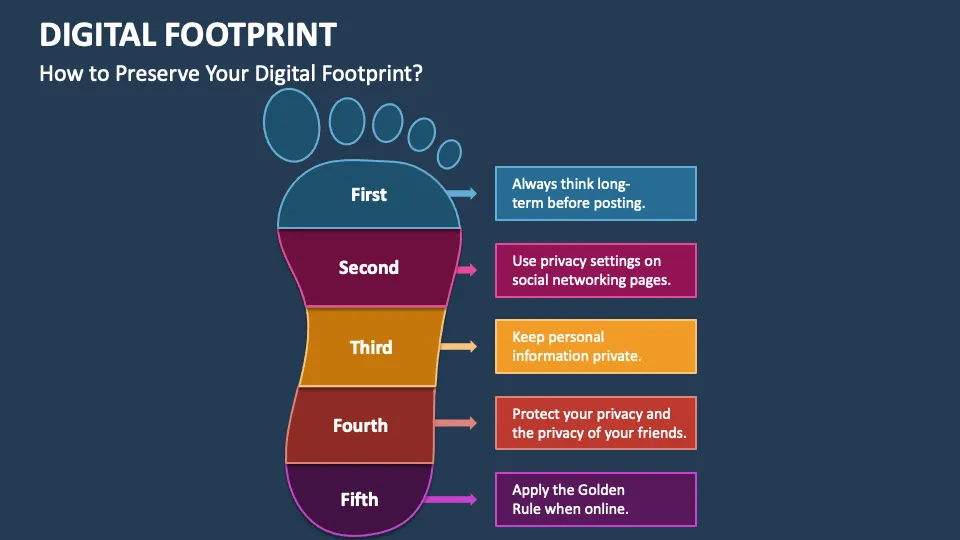
To control and limit your digital footprint, you need to proactively take the following measures:
Understand your digital footprint: The first step to protecting your personal information is to be clear about what you share online. Tracking your online activity can help you identify what data is vulnerable and adjust how you use it.
Check and adjust privacy settings: Make sure your social media accounts, apps, and platforms are configured to the highest level of security. Also, regularly review and revoke unnecessary access from third-party apps.
Be careful when sharing information: Avoid posting sensitive information such as personal addresses, bank accounts, lifestyle habits, etc. online. Any data you share can become a vulnerability if it falls into the wrong hands.
Use strong passwords and update them regularly: Use long, difficult-to-guess passwords that are different for each account. To manage them effectively, you can use secure password management tools.
Opt out of data collection and personalized advertising: Many platforms allow you to disable tracking and ad personalization. Enable these options to limit the amount of data that is mined.
7. Minimizing Your Digital Footprint: An Effective Way to Protect Your Privacy Online
Your digital footprint is the collection of data you leave behind when you access the internet, including device information, browsing behavior, and other identifying factors. Being proactive about controlling and minimizing this footprint will help you better protect your personal data and reduce the risk of being tracked or having your information stolen. Here are some reliable methods and tools to do just that:
7.1. Check digital footprint with dedicated tools
Platforms like iphey.com allows you to determine exactly what data is being collected and shared on the internet. With iphey, you can clearly visualize how your personal information is being tracked, thereby taking appropriate control measures.
This is just one of many tools that help check browser fingerprinting – you can use similar tools to see how much data websites are mining from your device.
7.2. Periodically delete cookies and browsing data
One of the simplest yet most effective ways to reduce the amount of data collected is to regularly clear your cookies, cache, search history, and location from Google. You can also install extensions that help manage cookies.
This not only limits the ability of websites to track you, but also helps improve your privacy when using the internet.
7.3. Use private browsing or anti-detection browsing
Incognito mode on browsers like Chrome only helps you not save your browsing history, but Google can still collect data during the session.
For a higher level of security, you should use an antidetect browser– specialized tools designed to completely hide the user’s identity. These browsers help create an absolutely anonymous environment, preventing the leakage of IP addresses, device information or browser fingerprints during web access.
7.4. Review and delete unused accounts
Maintaining multiple accounts that are no longer in use can leave you vulnerable to cyberattacks. Periodically review and delete accounts that are no longer needed to reduce the risk of data leaks from forgotten platforms.
7.5. Monitoring personal data breaches
Monitoring for personal data breaches helps you stay proactive in responding to any risks. Tools like Have I Been Pwned will notify you when your email or account is compromised on websites, helping you quickly change your password and increase security in time.
8. What is Hidemium Antidetect Browser? A Complete Anonymity Solution for Modern Users
In an increasingly invasive world of online privacy, preventing websites and advertisers from tracking your activity is more important than ever. Instead of relying solely on VPNs or proxies, many users are now opting for tools antidetect browsers like Hidemium– advanced solution for complete control device fingerprint and IP address.
With advanced anti-detection technology, Hidemium allows you to access the internet with near-absolute anonymity – even on highly-tracked platforms like Facebook or Google. The detection rate is almost zero, something that traditional VPN tools can hardly guarantee.
Originally developed as a security tool, Hidemium quickly became embraced by digital marketers as a powerful account management dashboard, and at the same time became a tool to support safe and effective remote work. Unlike conventional VPN services, Hidemium Do not collect or sell user data Instead, it's designed to enhance privacy from the get-go by preventing tracking rather than just temporarily masking identity.
Superior to traditional VPNs and proxies, Hidemium creates Brand new digital fingerprint, allowing you to operate on social networking platforms, e-commerce platforms or advertising tools without being detected, limited or blocked.
Hidemium Applications in Business
For small and medium-sized businesses (SMBs), safely running multiple advertising accounts and social networks like LinkedIn or Facebook is essential for sustainable growth. Hidemium helps businesses Freely manage and use multiple accounts at the same time without worrying about being flagged or blocked due to digital footprint duplication.
If you are running a business that needs anonymous browsing, digital identity protection or run multiple marketing campaigns at the same time, then Hidemium is the ideal solution. Not only that, it is also a tool effective in preventing identity-based attacks and reducing the risk of account loss.
>>> Learn more:Fingerprint browser when using Antidetect Browser software
9. Conclusion
Digital footprint is the data that users leave behind when using the Internet. They include passive trace– recorded without the user's knowledge (such as IP address, browser information), and active trace– directly generated by users, such as emails, social media posts, or online transactions.
Taking proactive control of your digital footprint is essential to protecting your privacy. You should regularly review your privacy settings, limit the information you share publicly, update your passwords periodically, and decline unnecessary data collection requests.
Among the tools available today, Hidemium Antidtect Browser is considered the optimal solution for anonymity needs - far superior to conventional VPNs or proxies thanks to its ability to create a whole new digital identity.
👉 Hidemium now offers a 3-day free plan with 1000 profiles– the perfect choice to start your journey of identity protection and safe web browsing. Download and experience it today!
Related Blogs
Have you ever felt tired eyes from constantly staring at the tiny phone screen to text? If so, you are not alone. With nearly 3 billion WhatsApp users worldwide, many of us are also looking for a more convenient solution.The good news is: WhatsApp Web is the perfect choice to help you get rid of that inconvenience. Now, you can chat on a large screen, type faster with a computer keyboard, and[…]
How to Get More Views on TikTok: 10 Proven Steps That Actually Work If your TikTok views are stuck or falling, the problem is rarely just “the algorithm.” The issue is usually a mix of content, targeting, and signals TikTok uses to decide who should see your videos.Here’s how to get more TikTok views using a simple system: diagnose what’s wrong, optimize your videos for discovery, post[…]
Cách Nhận Biết Antidetect Có Đang Bảo Vệ IP Thật Của Bạn. Ngày nay có rất nhiều phần mềm antidetect browser nổi lên, chiếm thị phần nhiều hơn và được quảng cáo rầm rộ là trình duyệt bảo mật an toàn nhất, fake thiết bị chuẩn nhất,… Nhưng đối với nhiều người thì khái niệm […]
Understanding a Facebook IP address not only helps enhance your account security but also aids in determining the user's location, allowing you to detect and prevent potential intrusions or fraud. So, what is a Facebook IP address, and how can you find it on your mobile phone? Let’s explore the details below with Hidemium Antidetect Browser.1. What is a Facebook IP address? Importance in web[…]






.png)