Websites are always on the lookout for bots. If your data collection tool is recognized as automated, it will be quickly blocked. Today, most platforms deploy advanced detection technologies such as CAPTCHAs, browser fingerprinting, and behavioral tracking to prevent bots.
When collecting data at scale for SEO, ecommerce, or market research, getting blocked not only wastes your time, but also results in incomplete data. The solution lies in disguising your crawler to act like a real user.
Hidemium is the tool that helps you do that. With the ability to emulate real browsers, integrate civilian IPs, and control fingerprinting, Hidemium helps crawlers hide more effectively and operate more smoothly.
1. How websites detect data collection tools
Websites use multiple layers of checks to detect bots. If your crawler doesn't mimic real user behavior, it's easy to get flagged:
IP Tracking: The website monitors the number of requests from each IP. Sending too many requests, abnormal speed or using a popular proxy/VPN will be easily blocked.
Browser fingerprint: Browsers share information like screen resolution, language, time zone, canvas… If your configuration is fake or duplicate, the system will detect it.
Behavioral analysis: Bots don’t usually move naturally. Websites will check mouse movements, scrolling, typing speed… to detect repetitive or too fast behavior.
JavaScript & CAPTCHA Check: Many platforms like Cloudflare, DataDome require the browser to run a script. If you fail to pass, you will be CAPTCHA or blocked.
Advanced blocking tools: Large systems like Akamai and PerimeterX combine multiple techniques—from IP scoring, fingerprinting, behavioral analysis to server logic—to thwart crawlers.
>>> Learn more: What is Canvas Fingerprinting? - The Latest Online Tracking Technology
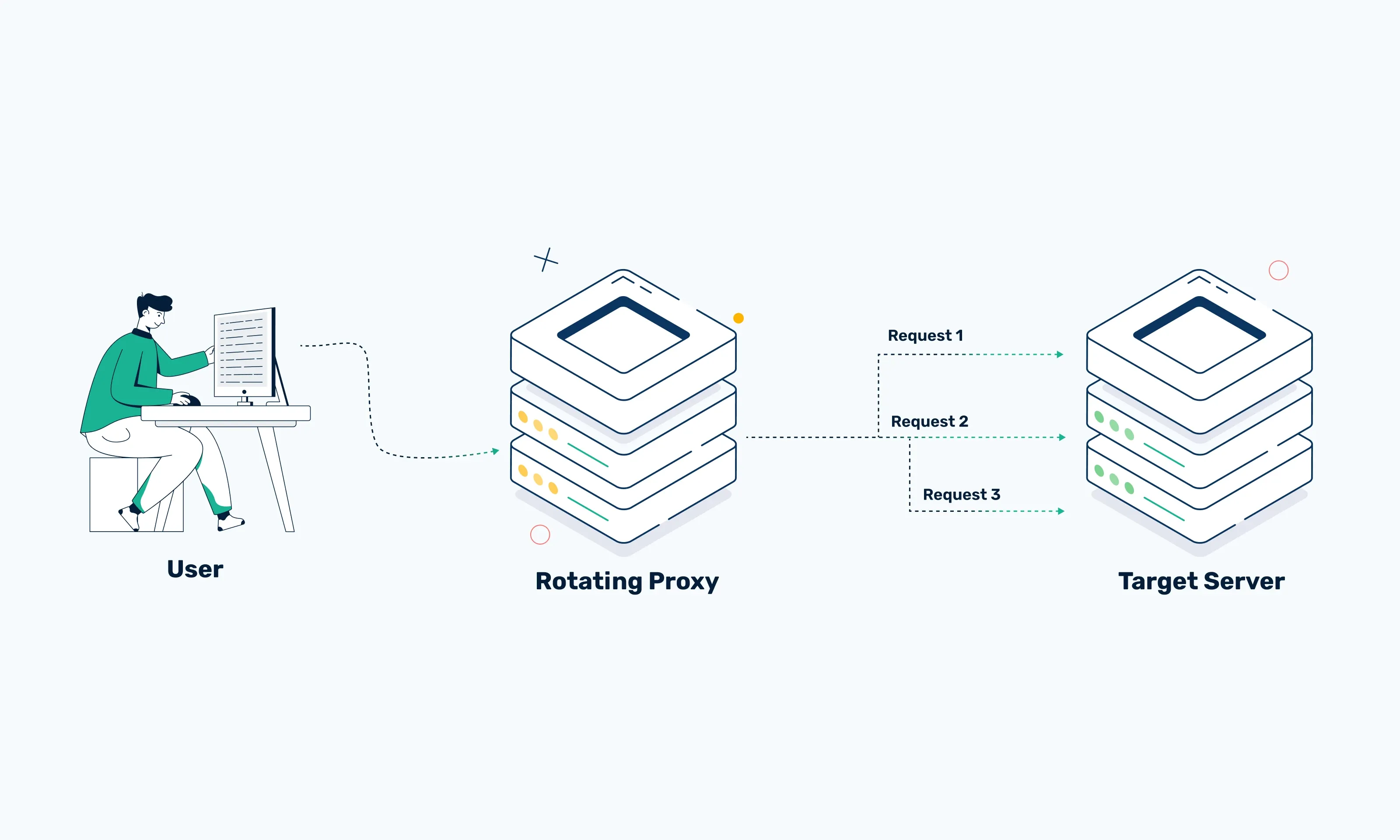
2. Why IP rotation alone is not enough
Rotating proxies can help you change your IP address to avoid being blocked, but they are only a basic and limited solution. Nowadays, most websites rely not only on IP checking but also on browser behavior analysis. If your tool sends too many requests, skips JavaScript, or fails to simulate real user actions, you are still vulnerable. Even if you change your IP, you are still at risk of CAPTCHAs, access restrictions, or silent bans.
Therefore, relying on IP alone is not enough. You need to ensure that the browser displays and operates like a real user, including fingerprint, user-agent, language, time zone, screen resolution, etc. Without these factors, the detection system can still easily recognize you.
3. How to hide data collector like real user
If a crawler looks like a bot, it will be labeled as a bot. So it’s important to “blend in” with a real user. This goes beyond IP swapping to emulating fingerprints and browser behavior. You need to make sure your IP, device, and system settings are in sync. The tool needs to know how to scroll, move your mouse, and click naturally.
Solutions such asHidemiumsupport you comprehensive optimization:
Fingerprint matches the selected proxy.
The browser profile is pre-warmed with real cookies.
Simulation environment for both desktop and mobile.
Anti-detection settings, bypass PixelScan and CreepJS checks.
When your bot behaves like a normal user, it won't be flagged. This is what makes data collection stable and sustainable.
>>> Learn more: Why blocking fingerprints doesn't prevent account bans
4. Tools and strategies to help hide scrapers effectively
For the scraper to work smoothly, you need to hide your tracks.
The anti-detection browser like Hidemium allows you to create multiple fake user profiles with unique IPs, fingerprints, and cookies. This makes each profile look like a real user, helping you avoid detection and blocking.
Proxy rotation is a must. Give priority to using residential proxies or mobile proxies that can change IP continuously and are suitable for the target location. Before subscribing to premium tools, you can save money on scrapers by checking active proxy and anti-detection browser deals curated by experts.
Additionally, the above tweaks Headless Browser helps tools like Puppeteer or Playwright behave like a real browser: enable image rendering, use real user-agents, randomize action patterns.
In some cases, you will need to CAPTCHA solver, however, only use it when other measures have not worked.
Custom tools vs. off-the-shelf tools: Off-the-shelf tools are often sufficient for common data collection tasks. But for complex or large-scale projects, developing your own toolset may be more optimal in the long run.
Remember, you don't need a lot of tools — just the right ones to make your scraper look natural and undetectable.
>>> Learn more: 7 Free Online IP Fingerprint Checker Tools
5. Why Hidemium was built to hide scrapers
The reason scrapers are often blocked is because they “look” fake.Hidemiumfixes that by recreating a complete browsing environment, simulating real user behavior — from fingerprints to time zones to device configuration.
With Hidemium, you don't need to bother setting up proxies, managing cookies, or constantly solving CAPTCHAs. Everything is built into a dedicated platform to bypass detection systems.
Hidemium's outstanding features:
Real browser profile with unique fingerprint
Built-in civil proxy, no manual entry required
Stable access sessions, long-term adhesion
Compatible with Puppeteer, Playwright and Selenium
Hide scrapers at scale, avoid detection
Comprehensive protection beyond IP: fingerprints, behavior, browser headers
Hidemium not only helps you hide the scraper but also makes it act as areal users.
6. Common mistakes that make scrapers easy to detect
Most data collection tools are blocked because they behave differently than real users. If you miss the basics, the detection system will quickly “catch” you. This not only results in data loss, but is also time-consuming and can lead to the entire account being banned.
Common errors encountered when running scrapers include:
Reuse the same IP or fingerprint: Once flagged, they are invalid across all platforms.
Sending too many requests in a short time: Real users can't reload a product page hundreds of times in just a few minutes.
Run bots in a browser without interface and without protection: Modern systems easily detect this mode.
Ignore the natural interactive behavior of the website: Pages typically expect scrolling, clicking, AJAX calls. If you ignore this, the traffic flow will be irregular and quickly blocked.
👉 In other words, for a scraper to work safely, it needs to simulate user behavior as realistically as possible.

7. How to Hide Scrapers Effectively
Use rotating residential proxies to hide IP
Residential proxies provide real IP addresses from users, helping scrapers “blend in” as normal access. Configure rotating proxies on a per-request or time-based basis to avoid IP abuse and blocking.
Combine IP with unique browser fingerprint
Every IP address must be accompanied by a browser fingerprint/separate (User-Agent, time zone, screen resolution, font, plugin…). If there are multiple IPs but the same fingerprint, the system can still easily detect. Tools such as Hidemium allows creation of thousands of independent fingerprints, ensuring 1–1 matching with each IP.
Simulate natural user behavior
Real users often scroll pages slowly, pause for a few seconds, click randomly or open a new tab. Scraper should replicate these actions instead of just sending a request directly to the server. Scripts in Hidemium can be used to simulate these actions, helping to bypass behavioral filters.
Periodically change User-Agent, cookies and sessions
Don't keep the information the same throughout the process. Every 20–30 minutes, change the User-Agent to a different Chrome/Firefox instance, refresh cookies, or create a new session to make the access data more natural.
Anti-detect browser automation
Browsers like Hidemium Support for hiding WebRTC, canvas, WebGL, font, timezone… makes scrapers difficult to track. You can run multiple profiles in parallel, each profile acts as a “real device”, much safer than using a normal headless browser.
Monitor blocking status and make timely adjustments
Always monitor server responses: CAPTCHAs, HTTP 403 errors, or unusual redirects are all warning signs. When they appear, change your IP, refresh your fingerprint, or slow down your crawl rate to avoid getting locked out.
👉 In short: For the scraper to operate stably and for a long time, it needs to be "completely camouflaged" from IP, fingerprint to access behavior. The most effective solution is to combine residential proxy + Hidemium + native behavior script, both saving effort and reducing the risk of being detected.
>>> Learn more: Fingerprint browser when using Antidetect Browser software
8. Conclusion: Hide scraper or accept being blocked
Data mining at scale is only effective when you avoid detection. Just rotating IPs is no longer enough. Websites are increasingly checking everything from fingerprints, behavior, headers to mouse movements.
If you want to keep your data stable and avoid the risk of being banned, you need to “disguise” your scraper as a real user with full control over IP, fingerprint, and browser behavior Hidemium helps you do it all in one single platform—no more complex pairing or depends on luck.
👉 Hidemium is now offering a 3-day free trial with 1000 profiles – the perfect choice to start your journey of identity protection and safe web surfing. Download and experience it today!
Related Blogs
Affiliate là một cách kiếm tiền online phổ biến hiện nay. Nhưng để gia tăng thu nhập từ Affiliate thì không phải ai cũng biết và áp dụng đúng. Vậy có những mẹo làm Affiliate nào hiệu quả? Cùng đi tìm câu trả lời qua bài dưới đây cùng Hidemium. Affiliate là gì? Affiliate Marketing […]
If your Amazon seller account is suspended, the most important thing is timely handling. This not only disrupts business operations, but also directly affects revenue and cash flow. The good news is that most suspensions can be reinstated if you understand the cause and know how to appeal properly.In this article, we will guide you through how to check your Amazon account suspension status,[…]
Digital Footprint, also known as digital footprint, is the sum of all the data you leave behind as you move around the Internet. Every click, post, share, or even search contributes to your online presence.So why does your digital footprint matter? Because it reflects your entire digital behavior – from what you disclose to hidden data like metadata attached to photos or browser information. This[…]
What is CCNP? This is one of the professional computer networking certificates globally recognized, by the world's leading technology corporation – Cisco Systems– level. For IT professionals, CCNP is not only a testament to their in-depth knowledge and practical skills, but also the key to opening up many opportunities for advancement and increased income.In the article below, togetherAntidetect[…]
How to Integrate IPRoyal with Hidemium — Complete Privacy at Your FingertipsIn today’s digital landscape, privacy, speed, and scalability are crucial. Whether you’re a digital marketer, developer, or eCommerce entrepreneur, managing multiple accounts and operations demands tools that are secure, seamless, and efficient.That’s why combining Hidemium with IPRoyal creates a powerful solution — one[…]